
Kerberos这一名词来源于希腊神话 三个头的狗——地狱之门守护者

Kerberos /ˈkərbərəs/ is a computer network authentication protocol which works on the basis of ‘tickets’ to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner.

is the act of confirming the truth of an attribute of a single piece of data claimed true by an entity.
is the function of specifying access rights to resources related to information security and computer security in general and to access control in particular.
Authentication is about who somebody is.
Authorisation is about what they’re allowed to do.
TGT: Ticket Granting Ticket
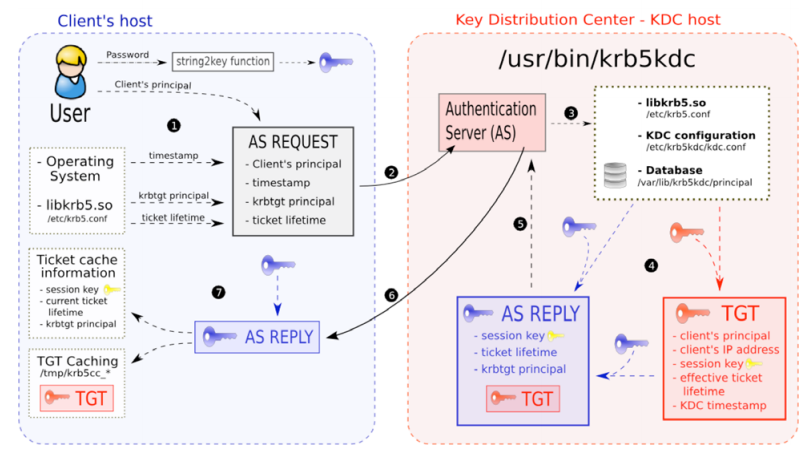
TGS: Ticket Granting Service
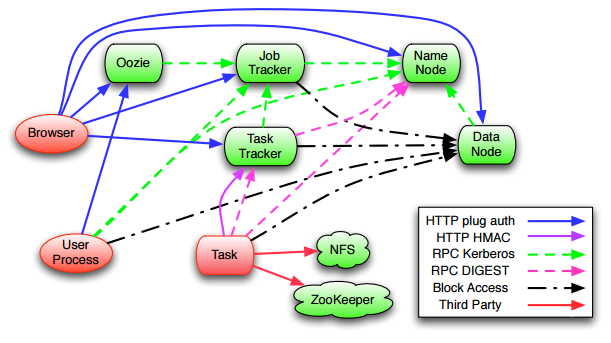
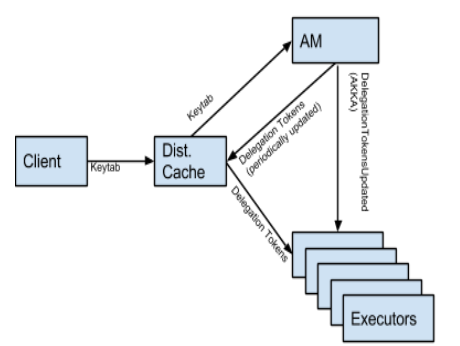
Spark-5342 Allow long running Spark apps to run on secure YARN/HDFS
Configuring YARN for Long-running Applications (Hadoop 2.6.0)
!java
// Log a user in from a keytab file. Loads a user identity from a keytab
// file and logs them in. They become the currently logged-in user.
static void loginUserFromKeytab(String user, String path)
// Log a user in from a keytab file. Loads a user identity from a keytab
// file and login them in. This new user does not affect the currently
static UserGroupInformation loginUserFromKeytabAndReturnUGI(String user,
String path)
// Return the current user, including any doAs in the current stack.
static UserGroupInformation getCurrentUser()
// Re-login a user from keytab if TGT is expired or is close to expiry.
void checkTGTAndReloginFromKeytab()
// Add the given Credentials to this user.
public void addCredentials(Credentials credentials)
public Credentials getCredentials()
// Run the given action as the user.
public <T> T doAs(PrivilegedAction<T> action)
!scala
UserGroupInformation.loginUserFromKeytab(principal, keytab)
val ugi = UserGroupInformation.getCurrentUser
A Subject represents a grouping of related information for a single entity, such as a person. Such information includes the Subject’s identities as well as its security-related attributes (passwords and cryptographic keys, for example).
!scala
val ugi = UserGroupInformation.getCurrentUser
!java
/**
* Perform work as a particular Subject.
*
* This method first retrieves the current Thread's
* AccessControlContext via AccessController.getContext,
* and then instantiates a new AccessControlContext
* using the retrieved context along with a new
* SubjectDomainCombiner (constructed using the provided Subject).
* Finally, this method invokes AccessController.doPrivileged,
* passing it the provided PrivilegedAction,
* as well as the newly constructed AccessControlContext.
*
* @param subject the Subject that the specified
* action will run as. This parameter may be null.
*/
public static <T> T doAs(final Subject subject,
final java.security.PrivilegedAction<T> action)
!scala
System.setProperty("java.security.krb5.realm", "HADOOP.QIYI.COM")
System.setProperty("java.security.krb5.kdc", "hadoop-kdc01")
Run once every day in crontab
!bash
kinit -l 3d -k -t ~/test.keytab test@HADOOP.QIYI.COM
!scala
val fs = FileSystem.get(new Configuration())
while (true) {
println(fs.listFiles(new Path("/user"), false))
Thread.sleep(60 * 1000)
}
Kerberos will relogin automatically, when token is expired
!scala
UserGroupInformation.loginUserFromKeytab(principal, keytab)
val fs = FileSystem.get(new Configuration())
while (true) {
println(fs.listFiles(new Path("/user"), false))
Thread.sleep(60 * 1000)
}
Kerberos will relogin automatically, when token is expired
Wrong:!scala
UserGroupInformation.loginUserFromKeytab(principal, keytab)
val fs = FileSystem.get(new Configuration())
while (true) {
UserGroupInformation.loginUserFromKeytab(principal, keytab)
println(fs.listFiles(new Path("/user"), false))
Thread.sleep(60 * 1000)
}
Do NOT call UserGroupInformation.loginUserFromKeytab again
!scala
val ugi = UserGroupInformation.loginUserFromKeytabAndReturnUGI(principal,
keytab)
ugi.doAs(new PrivilegedExceptionAction[Void] {
override def run(): Void = {
val fs = FileSystem.get(new Configuration())
while (true) {
println(fs.listFiles(new Path("/user"), false))
Thread.sleep(60 * 1000)
}
null
}
})
Kerberos will NOT relogin automatically, when token is expired
!scala
val ugi = UserGroupInformation.loginUserFromKeytabAndReturnUGI(principal,
keytab)
ugi.doAs(new PrivilegedExceptionAction[Void] {
override def run(): Void = {
val fs = FileSystem.get(new Configuration())
while (true) {
UserGroupInformation.getCurrentUser.reloginFromKeytab()
println(fs.listFiles(new Path("/user"), false))
Thread.sleep(60 * 1000)
}
null
}
})
Call reloginFromKeytab before token is expired
!scala
val creds = new org.apache.hadoop.security.Credentials()
val ugi = UserGroupInformation.loginUserFromKeytabAndReturnUGI(principal,
keytab)
ugi.doAs(new PrivilegedExceptionAction[Void] {
override def run(): Void = {
val fs = FileSystem.get(new Configuration())
fs.addDelegationTokens("test", creds)
null
}
})
UserGroupInformation.getCurrentUser.addCredentials(creds)
Update credentials periodically before token expired